Apple Troubleshooting
Check out our How-To's section under FAQ's, for the latest troubleshooting of Apple problems.
Check out our How-To's section under FAQ's, for the latest troubleshooting of Apple problems.
Being on top can get you a lot of attention. However, this limelight may not always be good for you. While most coders are happy to develop apps for popular platforms, some take the destructive route by writing malware. In computers, Windows has been dealing with these threats for a long time. Not surprisingly, Androids are now prime victims among smartphones.

According to the CA technologies (CA), they have found a new Trojan that can record calls from a victim's mobile. To test its abilities, CA's Dinesh Venkateshan ran the Trojan in an emulator. It was observed that the application pretends to be legitimate by showing approval prompts. Once, the permissions are given, the malware adds a remote server configuration file on the infected device. It then records every call and saves it to an AMR file on the phone's SD card.

Apart from slowing down your device, we suspect that this malware might even be able to upload recorded conversations to an online server maintained by the attacker or maybe the Murdoch's NewsCorporation.
Source:techtree.com
As smartphones penetrate every segment of the market, mobile malware is on the rise. And according to a new threat report from Lookout Mobile Security, Android is taking the brunt of the attacks.

The Achilles heel of Android security is also a source of strength for the platform, as the open marketplace model that Google has used to propel its mobile OS to global prominence serves as an open vector for an array of malware attacks. Here are eight of the most pernicious malware threats Android has suffered so far.
1. Fake Banking Apps
In 2009, while the Android Market was still in its infancy, a user known as Droid09 uploaded several phony online banking apps to lure customers of major banking institutions into entering their online account logins. "Informed of this, Google quickly removed them," said Robert Vamosi, senior analyst at Mocana and author of When Gadgets Betray Us.
2. Android.PjappsM
Early in 2010, sly attackers downloaded legitimate programs from the Android Market, infected them with the Android.Pjapps malware, and then redistributed the modified versions on third-party Android marketplaces. The objective, according to Symantec, was to steal information from infected devices and enroll the device in a botnet that then launched attacks on websites to steal additional data and infect more devices. It also sent costly SMS messages.
3. Android.Geinimi
While not too worrisome for North American users, the Trojan horse known as Geinimi corrupted a number of legitimate Android games on Chinese download sites, and added infected devices to a mobile botnet.
4. AndroidOS.FakePlayer
While relatively ineffective against U.S.-based targets, the AndroidOS.FakePlayer threat demonstrated how easily an attacker could steal from users without their knowledge. As Symantec explained, "This malicious app masquerades as a media player application. Once installed, it silently sends SMS messages (at a cost of several dollars per message) to premium SMS numbers in Russia." Fortunately, it didn't work on wireless networks outside of Russia, so the actual damage was minimal for North American wireless customers.
5. DroidDream (aka, Android.Rootcager)
One of the most nefarious malware campaigns addressed in Lookout's Mobile Threat Report, DroidDream infected roughly 60 different legitimate apps in the Android Market and infected hundreds of thousands of users in the first quarter of 2011. The malware added infected devices to a botnet, breached the Android security sandbox, installed additional software, and stole data.
6. Android.Bgserv
Shortly after Google deployed a tool for users to clean up devices that had become infected with DroidDream, malware authors got clever and, according to Symantec, "attackers capitalized on the hype and released a malicious fake version of the cleanup tool." Known as Android.Bgserv, this somewhat less dangerous bit of malware stole device data, such as the phone's IMEI number and phone number, and uploaded it to a server in China.
7. GGTracker
As Android threats continue to evolve, malware creators are getting increasingly clever about luring users into downloading their malicious creations. In June of this year, a threat called GGTracker presented users with a mobile Web page designed to look like the official Android Market, and prompted them to download a phone battery-saving app. Once installed the app sent premium SMS messages from users' phones, charging rates of up to $40 per message.
8. DroidKungFu
In an emerging malware distribution tactic known as an update attack, malware creators weasel their way into the app store with a legitimate app, wait for a significant number of users to install it, and then inject malware into the app via an over-the-air update. The first known example of this, DroidKungFu, was thwarted before it could infect users on the official Android Market. Security analysts at Lookout spotted in on Chinese markets, and then noticed the same writers attempting to post it to the Android Market. Lookout notified Google, and the app was immediately rejected.
Attend Enterprise 2.0 Santa Clara, Nov. 14-17, 2011, and learn how to drive business value with collaboration, with an emphasis on how real customers are using social software to enable more productive workforces and to be more responsive and engaged with customers and business partners.
Source:informationweek.com
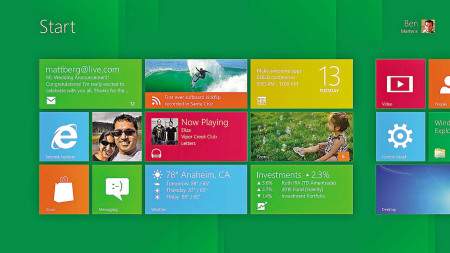
Yes, here we go again. No sooner have we all become comfortable with Windows 7 and Microsoft is gettingready to release the next version of Windows, Windows 8.
The good news is that this newest version will require the same hardware specifications as Windows 7, so that shiny new computer you may have just purchased will not suddenly be obsolete when Windows 8 comes to market.

While that has been welcome news to many, the other good news is that software and, more importantly, things like printer drivers and other similar software required to run all the devices that you connect to your PC will also work with Windows 8 out of the box. This too, will be welcome news to many. Since the introduction of the first mainstream version of Windows, Windows 95 in 1995, some of the new versions of Windows have raised havoc with software, printers and more. Microsoft has clearly learned from these mistakes and Windows 8 will not repeat them.
It's interesting looking back, that there have been seven versions of Windows over the past 17 years. Over that time, we have seen Windows 95, Windows 98, Windows Me, Windows 2000, Windows XP, Windows Vista and Windows 7. That's a new version of Windows approximately every two and half years.
That's a lot of change in a short amount of time. And we are on the cusp of some significant new changes, in part driven by the success of smartphones and tablets, namely Apple's iPhone and iPad.
Windows 8, while largely based on the stability and success of Windows 7, will have a distinctly new look and feel. This new look and feel screams touch, as in touchscreen. Yes, Microsoft is recognizing that touch is the new mouse. While the traditional computer will still run Windows with a keyboard and mouse, the interface will still look touch oriented. It's oriented to swiping motions across the screen, what you are accustomed to with a smartphone and tablet.
Microsoft has clearly invested in an operating system that will unify the experience across all three platforms, PC, smartphone and tablet. We have already seen this evolution in the nascent Windows Phone 7 and it will only accelerate from there.
I spent some time at Microsoft's New England office this week and saw the new operating system demonstrated firsthand. It runs well on mainstream hardware and definitely benefits from a touch-screen capable computer.
What will be most notable is that the start button is gone in Windows 8, replaced by a start screen that is presented as multi-color tiles across the screen, with additional screens to the side that you can pull into focus just like you do on a smartphone and tablet. Are you sensing a theme here? Even the way you interact with a wireless network will resemble the way you do on a smartphone or tablet as compared to how you do it on a computer today.
It's a true evolution in how we interact with our PCs and it should herald increased productivity in that our user experience across any device we use will be more familiar and easier to interact with. These are good things.
However, the transition to Windows 8 will not be without its pitfalls. This is a major design evolution that will likely intimidate many computer users, just due to the obvious visual changes. As with any significant new software release, you probably don't want to jump right in. Let others learn the lessons of the early adopters.
It's important to know what the future holds, but most businesses do not have a compelling justification to be the first to upgrade as soon as something new becomes available.
See how the market adjusts to the new version of Windows and then work with your IT staff or partner to come up with a sensible plan to test out and implement the new version at the right time for your business.
There is no question the new version of Windows will be an important development in the world of business and technology.
The new version is slated to be available in October of this year.
A "consumer preview" is available now for those who like to download and play with the latest versions of software before they are released in final form. If you're that type of person, it's a great time to check it out.
Otherwise, it's good to be aware of what's coming and start the conversations about when you will begin to introduce the newest version to your computer users.